- June 17, 2021
- Posted by: admin
- Category: BitCoin, Blockchain, Cryptocurrency, Investments
A new attack vector following the Ledger data breach of July 2020 involves sending convincing but fake hardware wallets to victims.
Victims of a hack of customer data held by bitcoin hardware wallet provider Ledger, which happened almost a year ago, are still apparently being targeted by scammers. Over 1 million victims of the hack had their details exposed, including their names, phone numbers and email addresses. And more than 200,000 people also had their home addresses breached.
Now, some of the victims appear to be receiving counterfeit hardware wallets through the mail. And a recent Reddit post indicates that the new scam attempt is quite sophisticated.
Reddit user u/jjrand, who self-identified as one of the victims of last year’s Ledger data breach, shared that they received a package that appeared to be from Ledger in the mail, even though they hadn’t ordered one. Although the device was wrapped in seemingly authentic packaging, the user could spot some telltale signs that hinted that it was a fake. The package also included a letter, supposedly from Ledger CEO Pascal Gauthier, though it was poorly written and filled with grammatical and spelling errors.
“As you know, Ledger was targeted by a cyberattack that led to a data breach in July 2020,” read the fake letter. “For this reason for security purposes, we have sent you a new device you must switch to a new device to stay safe. There is a manual inside your new box you can read that to learn how to set up your new device. For this reason, we have changed our device structure. We now guarantee that this kinda breach will never happen again.”

Also in the package was a Ledger Nano X box that seemingly contained a legitimate device. However, the Reddit user became suspicious and opened it, sharing pictures demonstrating that the machine was likely tampered with.

Security researcher Mike Grover analyzed the photos and explained to BleepingComputer how the attackers probably carried out their actions.
“This seems to be a simple flash drive strapped on to the Ledger with the purpose to be for some sort of malware delivery,” Grover told BleepingComputer in a chat about the photos. “All of the components are on the other side, so I can’t confirm if it is JUST a storage device, but…. judging by the very novice soldering work, it’s probably just an off-the-shelf mini flash drive removed from its casing.”
Grove also explained that “those four wires [highlighted in the photo] piggyback the same connections for the USB port of the Ledger.”
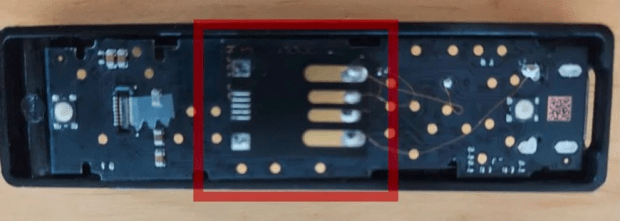
Previously, the attackers had sent out phishing emails to victims, prompting them to type in their recovery seeds — the 12 or 24 words used to derive one’s private keys, giving anyone who possesses it complete control of the victim’s funds. By tampering with the device, the attackers likely hoped to get their target to type their recovery words into the fake application, which would allow the bad actors to take control of the victim’s funds.

Therefore, this attack is severe since it could cause a victim to lose all of their funds. Ledger is already aware of this scam and warned users in a post in May.
“The fake user guide in the Nano’s box asks the user to connect the device to a computer,” the post stated. “To initialize the device, the user is then asked to enter his 24 words in a fake Ledger Live application. This is a scam. Do not connect the device to your computer and never share your 24 words. Ledger will never ask you to share your 24-word recovery phrase.”
It is unclear if Ledger has done any active work to educate its customers who saw their data exposed last year with dedicated emails or warnings, apart from the passive blog posts.
Needless to say, under no circumstance should you type your bitcoin wallet seed phrase on any keyboard, take photos of it or have any internet-connected device know about it. The only safe place to store, write and recover a seed phrase is the hardware wallet itself.
More On Bitcoin Seed Phrases And Private Keys
A seed phrase is a collection of 12 or 24 human-readable words used to generate bitcoin private keys for a wallet. The seed phrase, also known as the recovery phrase or backup phrase, contains all of the information needed to access, spend and recover bitcoin funds. For this reason, the seed phrase has to be kept safe; otherwise, anyone who discovers it can steal the bitcoin.
The private key, which is generated by the seed phrase, is not human readable. It is a secret 256-bit number, usually in hexadecimal format — 64 characters or 32 bytes in the range of zero to nine or A to F.
Modern wallets leverage both seed phrases and private keys to employ Hierarchical Deterministic (HD) Wallets, using BIP32 seeds. HD Wallets allow the wallet to use a single seed phrase to generate a whole sequence of keys, allowing the entire wallet to be restored from that seed.
