- May 1, 2021
- Posted by: admin
- Category: BitCoin, Blockchain, Cryptocurrency, Investments

Earlier this week, Uranium Finance, a Binance Smart Chain-based DeFi project, claimed to have lost $50 million dollars in an exploit of its platform, which had borrowed code extensively from Uniswap, a leading decentralized crypto exchange that runs on the Ethereum blockchain.
An automated market maker (AMM) protocol, it is a fork of Uniswap V2, with the added bonus of providing users with daily dividends to its users.
The Uranium developers had only recently deployed Version 2 of their contracts, just eleven days prior to everyone migrating to v2.1. The project tweeted upon the exploit:
“Uranium migration has been exploited, the following address has 50m in it The only thing that matters is keeping the funds on BSC, everyone please start tweeting this address to Binance immediately asking them to stop transfers.”
They then apparently took to the Telegram group for Binance users and developers, Binance Chain (BC) & Binance Smart Chain (BSC) – Developments Discussion Group, seeking help:
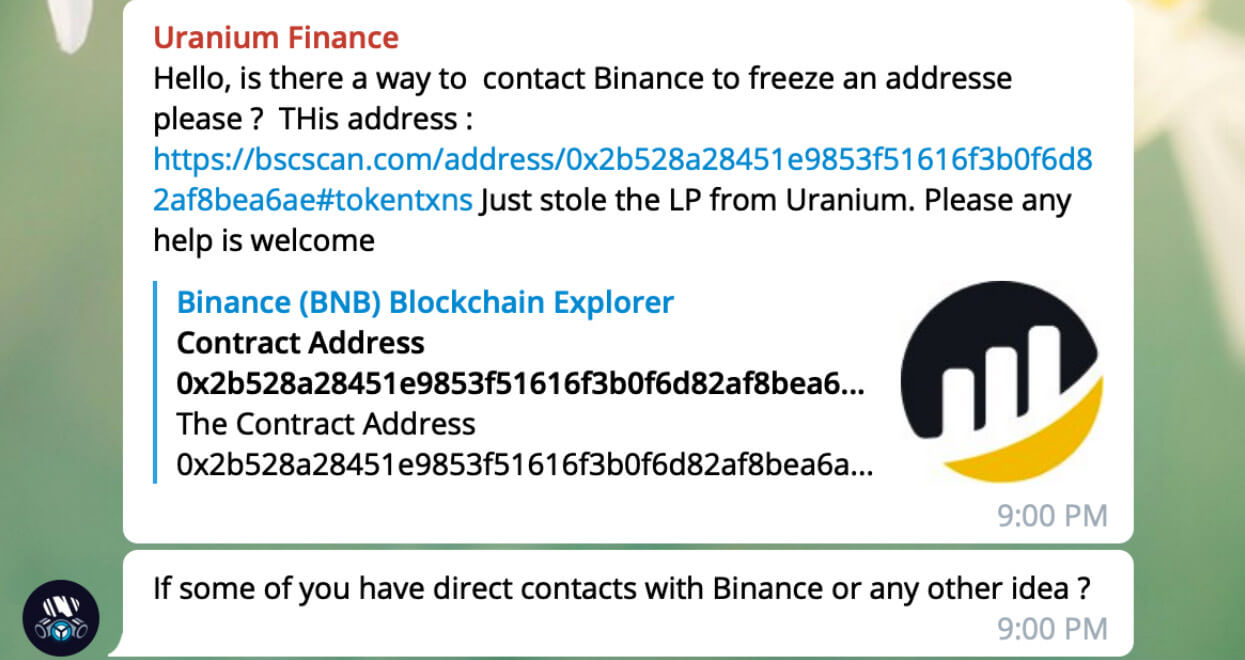
We can only presume that was the project’s reps posting. All-in-all, here’s a list of what was stolen:
- 80 bitcoin ($4.3 million)
- 1,800 ETH ($4.7 million)
- 17.9 million BUSD ($17.9 million)
- 5.7 million USDT ($5.7 million)
- 638,000 ADA ($0.8 million)
- 26,500 DOT ($0.8 million)
- 34,000 wrapped BNB ($18 million)
- 112,000 U92 tokens
Before interacting with Uranium, which launched earlier this month, the attacker sent the minimum amount of each token to pair contracts and then employed a low-level “function swap(),” which is a computer programming function that could be used to drain both reserves.
(1/2)
Uranium migration has been exploited, the following address has 50m in it The only thing that matters is keeping the funds on BSC, everyone please start tweeting this address to Binance immediately asking them to stop transfers.
— Uranium Finance (@UraniumFinance) April 28, 2021
“In our pools and farms, you’re rewarded with our U92 token, like every other DEX [decentralized exchange],” reads Uranium’s website. “The difference is that we have created a second token, the U92 counterpart: U235. Holding this token on your wallet makes you an investor of our AMM, making you earn dividends in BNB and BUSD every block.”
According to The Block’s research analyst Igor Igamberdiev, pair contracts in Uranium’s V2 version had contained the bug which enabled the exploit. They did this by allowing anyone to interact with the pair contracts, which are smart contracts for trading pairs in an AMM and withdraw all of the tokens.
The exploiter used a swap function in Uranium to drain the funds, which were then, at once, transferred — $6.4 million or 2,438 ETH had been withdrawn via Tornado Cash, an Ethereum mixer allowing users to withdraw funds anonymously. The hacker at first swapped DOT and ADA tokens to ETH via Pancake, the Binance Smart Chain-based decentralized exchange.
All 80 BTC were withdrawn by the hacker using AnySwap, which is a fully decentralized cross-chain swap protocol. Users swap between any coins on any blockchain.
Suspiciously, the Uranium contracts repository was removed from GitHub. There’s been no explanation as to why. Yet, you can still see the problematic code with a little but of research.
Kyle Kistner, co-founder of bZx, on the original code from the Sushi repo that Uranium forked:
Here's the original code from the Sushi repo that Uranium forked: pic.twitter.com/QKVkpm3KVh
— Kyle "1B TVL" Kistner | Fulcrum | bZx (@BeTheb0x) April 28, 2021
And the Uranium devs code:
Now here's the code used by the Uranium devs:
See the difference? 1000 was changed to 10000 in two places but not the end. The result? You could swap 1 wei of the input token for 98% of the total balance of the output token. pic.twitter.com/c8pRD55Fe9
— Kyle "1B TVL" Kistner | Fulcrum | bZx (@BeTheb0x) April 28, 2021
In short, Uranium Finance got too creative with borrowed code. At least $57,000,000 has been taken in this exploit, making it the second-largest DeFi exploit behind EasyFi’s $59,000,000 hack. Uranium Finance had already suffered an exploit of their rewards contract earlier this month due to vulnerabilities in one of the project’s smart contracts.
Kyle Kistner, the co-founder of bzX, highlighted the fact that small changes in the UraniumPair contract had dramatic effects on how the code behaved. He also notes that the Uranium team seemingly knew about the exploit beforehand. “If you diff v2 and v2.1, the only change is to remove the exploit,” he tweeted.
Summing up the hack, Ape Developer, ChartEx Pro Core Developer:
“This looks like a $50m typo, not really an interesting hack. Just an expensive mistake. Something that should have been trivial to pick up with very basic unit testing. It is clear from the swap function they forked that of Uniswap (similar comments, same order, identical code). Copy-pasting pieces of different protocols leads to results like this.”
The post The most recently hacked DeFi project couldn’t even copy and paste Uniswap and Sushiswap’s code appeared first on CryptoSlate.
